Summary:
No Rate Limit – Bug Hunting: In computer networks, rate limiting is used to control the rate of traffic sent or received by a network interface controller and is used to prevent DoS attacks.
What is Rate Limiting..?
Rate limiting is used to control the amount of incoming and outgoing traffic to or from a network. For example, let’s say you are using a particular service’s API that is configured to allow 100 requests/minute. If the number of requests you make exceeds that limit, then an error will be triggered
No rate limit means there is no mechanism to protect against the requests you made in a short frame of time. Say for example you have a forgotten password page and a victim’s email, now enter the victim’s email and intercept the request using a burp suite (a proxy tool) and send that request to the repeater or intruder for repeating it. If the repetition doesn’t give any error after 50, 100, 1000 repetitions then there will be no rate limit set.
Now the scope of this vulnerability is not limited only to forget password page you can also use it in comments, adding user (where you need to send an invite email), sending GIFs or messages, sending OTPs, etc.
While searching for No rate limit I came across a forgot password page at some x website let us assume it as a www.example.com which doesn’t have a rate limit.
Step-1: Go To This Link: https://example.com/forgot-password
Enter Email Click On Forget Password
Choose forgot password option
Enter Email Click On Reset
Step 2– Intercept This Request In Burp And Forward Till You Found Your
Number In Request Like user=user_email_id
POST /users/reset.json HTTP/1.1
Host: api.example.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 37
Origin: https://example.com
Referer: https://example.com/forgot-password
Connection: close
user=user%40gmail.com
user :"[email protected]"Step 3: Now Send This Request To Intruder And Repeat It 100 Time By Fixing Any Arbitrary Payload
Which Doesn’t No Effect Request I Choose Accept-Language: en-US,en;q=0.$5$
Step 4 – See You Will Get 200 ok Status Code & 100 + Email In Your INBOX
See It Is Resulting In Mass Mailing Or Email Bombing To Your Users Which Is Bad For Business Impact
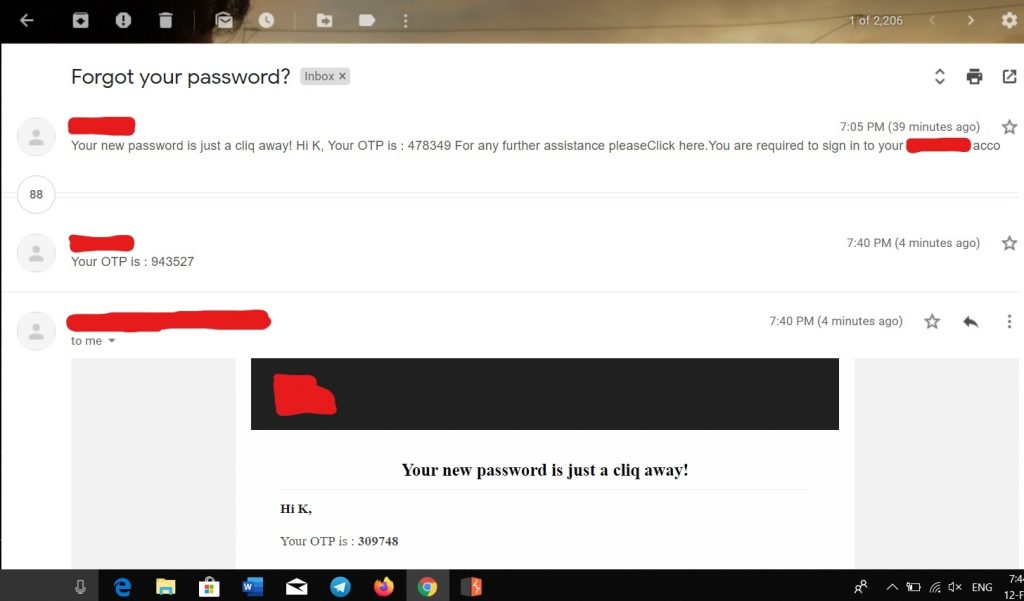
Impact:
If the website is Using Any Email Service Software API Or Some Tool Which Costs You For Your Email This
Type Of Attack Can Result in company In Financial Lose And It Can Also Slow Down Your Services It Can Take
Bulk Of Storage In Sent Mail Although If Users Are Affected By This Vulnerability They Can Stop Using
Your Services Which Can Lead To Business Risk
Solution
I Will Recommend websites To Add A ReCaptcha & Sort Of Something Which Requires Manual Human
Interaction To Proceed Like You Can Add Captcha Like 2+2=_ so that it cannot be brute-forced and
you also can have a limit at the backend for particular number up to 5 times a day user can request Forget
Password Email or Link something like that will prevent you from someone exploiting this vulnerability
